Not many of you may know that MS Excel offers special security measures. These might be used for various reasons, and we can divide them from really basic, like securing a workbook with a password, to more advanced ones requiring user authentication and role-based access.
In logistics, it is important to allow certain people access to workbooks and also limit their access once they are no longer assigned to a certain role. This is unusual because when you take security measures in logistics to protect a workbook, you're not doing it just because someone might steal your data. You need to limit access to prevent employees from accidentally opening a file and, for example, overwriting it with a new version. This often leads to some data being deleted from the workbook. So, it's crucial that the right people can enter the password and others have a role with restrict editing.
We dedicate this article solely to logisticians with relevant experience working with MS Excel. This material is also helpful for logistics managers who want to better protect their customer data and ensure their business won't be jeopardized due to a lack of proper measures, such particular password protection. You'll better understand how to do all this for free in Microsoft Excel. Look at our short MS Excel file techniques and methods to protect logistics data!
Why use Excel security systems like password protection and others?
There are several crucial factors for using Excel security systems. There is no doubt that in 2024 and beyond, Excel files will remain a widely used tool in logistics. Warehouse clerks and office staff use it to track shipments, manage inventory, and calculate costs. This is kept in Excel workbooks that various people can access to share files. However, its widespread use also makes it a target for data breaches and unauthorized access. This happens both internally and externally.
One example of a security breach in logistics involves an Excel workbook file downloaded from suspicious sources. After opening the file, users on the PC were asked to enable macros at the top of the Excel file interface. Once enabled, the macro ran an extended code that changed our system settings, making the network more vulnerable. Why were they downloading this? Often, users search for Excel templates to make their job easier, but it is important to know from where it was downloaded.
Files of the same type are often sent to mailboxes as normal attachments. Unaware staff in the office may open the file and enable the macro in the same way. The damage could be small, or hackers might use more sophisticated methods, such as using your Outlook mailbox to forward all emails to their mailbox. How data breaches can occur is virtually limitless. This is how a lot of private data can become public instantly. Therefore, strong Excel security systems are crucial to protect sensitive logistics data and maintain operational efficiency.
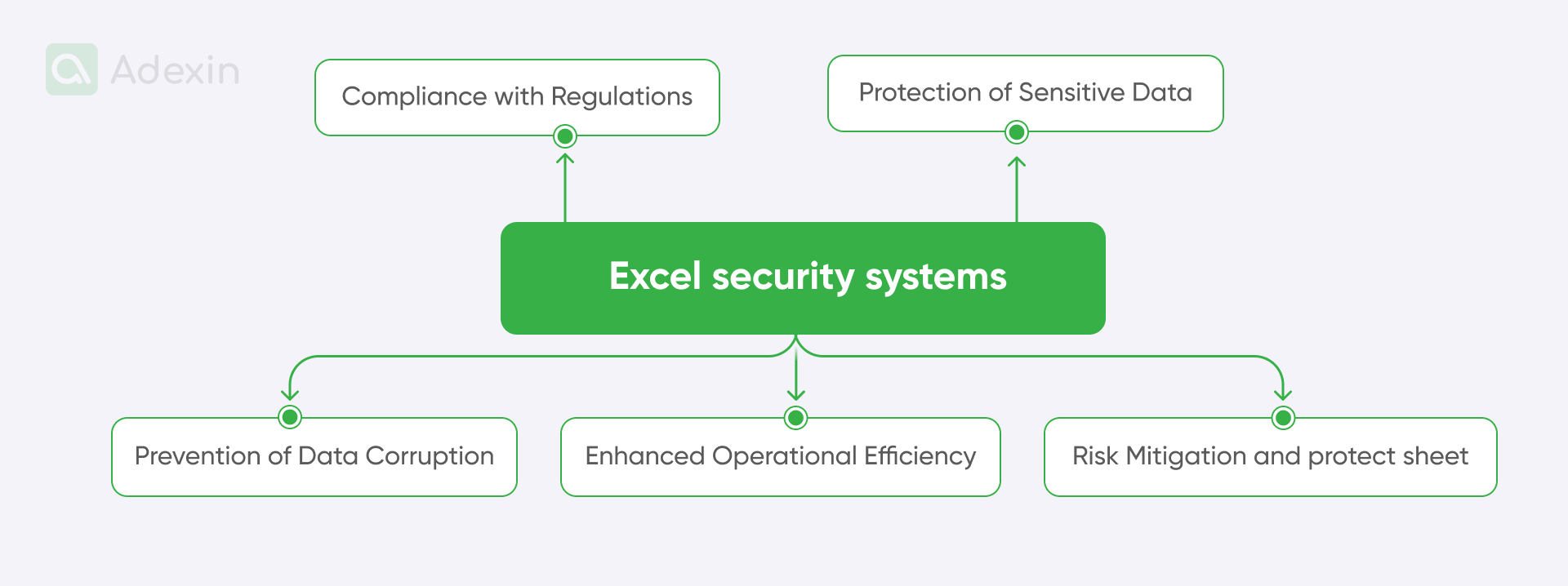
Here are some key reasons why Excel security systems are essential in logistics:
Protection of sensitive data based on password protection
Logistics data often includes confidential information such as customer details, shipment tracking numbers, or even financial data with invoices. Excel security systems can help prevent unauthorized access to this data with password protection, reducing the risk of data breaches and even serious financial losses.
Compliance with regulations
Industries such as logistics are subject to strict data privacy regulations like GDPR and CCPA or even data protection obligations imposed by their customers in contract logistics. Excel security systems can help ensure compliance with these regulations by implementing measures to protect personal data and business.
Prevention of data corruption with worksheet protection
Accidental or intentional modifications to logistics data by unauthorized users, such as warehouse clerks, can have significant consequences. Excel security systems can help prevent data corruption. For example, restricting access to certain cells or locking down entire workbooks can prevent the loss of a lot of data.

Enhanced operational efficiency
When you protect data in your logistics and prevent unauthorized access, you can run an error-free business. Any complications with data loss can boil down to severe problems. For example, secure access controls can ensure that only authorized personnel access sensitive data, reducing the risk of errors and delays.
Risk mitigation and protection sheet
Deploying Excel security systems can help mitigate the risk of data breaches and prevent reputational damage. By protecting sensitive data, you, as a logistics company, can build trust with your customers and partners.
What are Excel security settings?
Security settings are the various options available to control who can access a computer, network, or account, and what they can do once they're granted access. The most basic security setting is a password, which helps to ensure that only authorized users can gain access.
In this article, we'll examine how to protect an Excel sheet from editing and copying, lock an Excel document, and many other security settings. We all know that Excel offers a variety of security settings to safeguard sensitive data.
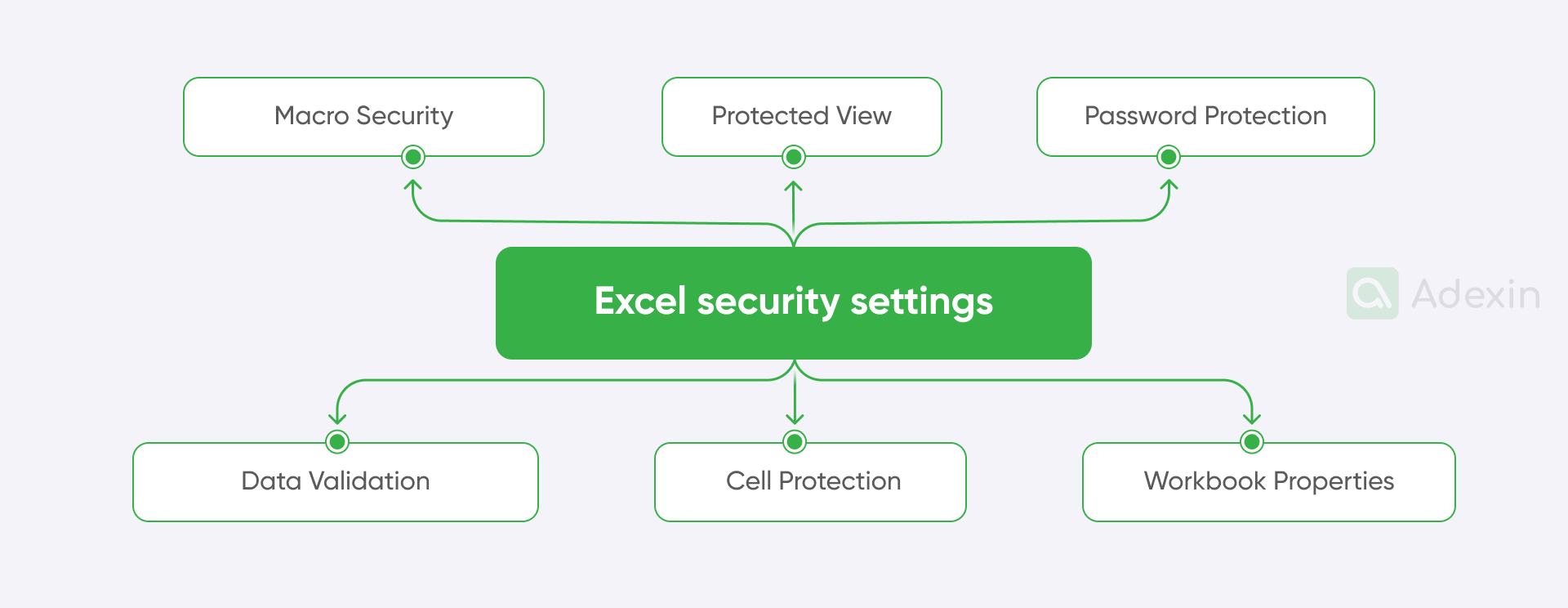
Here are some key areas to consider:
1. Macro security Excel file:
Disable all macros. This is the most restrictive setting as a typical data breach example from outside. It prevents any macros from running. However, it can also limit the functionality of legitimate workbooks. So, you may be unable to use Excel automation without macro.
Disable all macros except for trusted macros. This setting strikes a good balance between security and functionality. It allows macros from trusted sources to run while preventing potentially malicious macros from executing.
Enable all macros. If you're 100% sure, you can use this setting as the least secure measure open. It allows all macros to run without any restrictions. It should only be used in trusted environments, so basically, only in your network.
2. Protected view in Excel files:
Enable protected view for Outlook attachments. This setting prevents potentially unsafe attachments from opening automatically when received via email. This also refers to our example from above because some attachments can open automatically once downloaded. This will be equal to any data breach.
Enable protected view for files downloaded from the Internet. This setting prevents files downloaded from the Internet from opening automatically. This is also relevant to our example given above, as you protect files against opening, reducing the risk of malware infections.
Enable protected view for files from untrusted locations. This setting prevents files from being in untrusted locations. So, once you get an email from an unknown sender, you may see directly that this email is out of your network. It is protection against opening removable drives or shared network folders from opening automatically.
3. Password protection:
Open password. This password protects the workbook from being opened without the correct password. This is very useful in logistics and internally, as you simply prevent users from other departments from looking into data.
Modify the password for the Excel workbook. This password protects the workbook's structure and content from being modified without the correct password. Commonly, the secure structure in an Excel file can have gaps, and users who are not allowed to enter the file can still change it. The difference between these role assignments is that one is file-based, and the other is an MS account-based role. So, one can be on top of another, and users can still change their password.
Both passwords can be set independently. This secure setting means that you can always change the password just in case, as long as your administrator allows it.

4. Data validation:
Input message. This Excel logistics function provides a clear and concise prompt to guide users when entering data into a cell. So, when you have any file, for example, you could use an input message like "Please enter a valid email address" or "This file is incorrect" in a cell designed for email addresses. This helps prevent users from entering incorrect or irrelevant data in the Communication Matrix for logistics.
Error message. This displays a message to the user when they attempt to enter invalid data. Quite often, you can set up rules for the entire organization. For instance, you could set up an error message with a dialog box like "Invalid date format." This can be used if a user enters a date in the wrong format. Error messages deter users from entering incorrect data and can help maintain data integrity.
5. Cell protection:
Lock cells. You can also lock cells, which prevents users from editing or deleting their contents. This is especially useful for protecting sensitive data or ensuring that formulas are intact. It also concerns how some users can accidentally remove something that we don't want them to do. For example, you might lock cells containing financial data or formulas to prevent accidental changes.
Hide formulas. Hiding formulas prevents others from seeing the underlying calculations in a cell. It can protect intellectual property or simply make the workbook easier to read and understand. For example, in logistics, you could hide complex formulas to simplify the appearance of a dashboard, but the way you do this doesn't have to be sophisticated. It's enough if you hide some rows of columns.
6. Workbook properties:
Author. MS Office has this particular function that specifies the name of the person who created the workbook and edited it as the last. It can help track ownership and accountability.
Comments. To protect data, you can also use a particular function in Excel, comments in the review tab. This allows you to add additional notes or instructions to the workbook for other employees. Comments can provide context or even explain specific calculations. This is an amazing way to offer guidance to other users.
Are you in search of a reliable tech partner?
Adexin can help with advanced logistics solutions
Contact usFinal takeaway
By effectively utilizing Excel's primary functions, such as data validation, cell protection, and workbook properties, you can find a great way to significantly enhance the security and integrity of your data. It can be done cost-effectively, as tools like Excel are free. Excel also offers features that help prevent errors and better protect sensitive information. You can achieve many benefits and improve collaboration by taking the above-mentioned measures.
We have spoken with logistics companies, and we know that implementing all these measures is not always easy. At Adexin, we help logistics businesses protect their data and ensure smooth business integration. Given that Excel has many challenges, we also dedicate a large volume of work to logistics software development and assist with Excel automation and integration. Contact us to discover how our Excel security solutions safeguard your valuable data and streamline your workflows.


